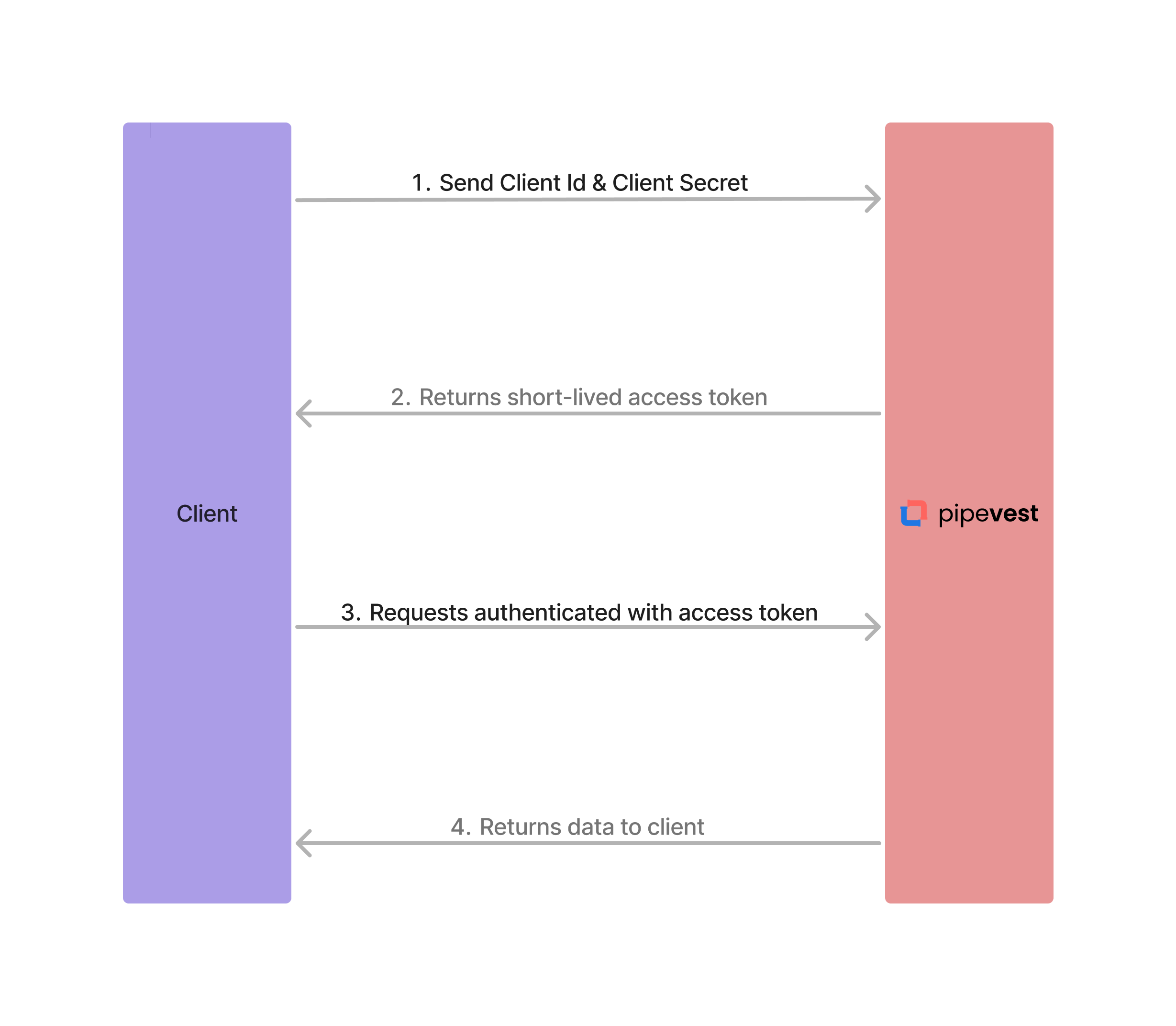
OAuth 2.0 All API endpoints are authenticated using OAuth 2.0 standards. A client Id and client secret
must be exchanged for a shortlived access token. This access token is then used to authenticate further requests.
Auth Flow Diagram The following diagram illustrates the authentication flow with Pipevest.
Usage
Access Token Request
curl --request POST \ --url https://api.pipevest.com/v1/oauth/token \ --header 'Content-Digest: sha-512=:RK/0qy18MlBSVnWgjwz6lZEWjP/lF5HF9bvEF8FabDg=:' \ --header 'Content-Length: 18' \ --header 'Content-Type: application/x-www-form-urlencoded' \ --header 'Signature: ...' \ --header 'Signature-Input: ...' \ --data 'clientId=<client-id>' --data 'clientSecret=<client-secret>'
Authenticate Requests with Token
The access token is passed into the authorization header as a bearer token
curl --request GET \ --url https://api.pipevest.com/v1/customers \ --header 'Signature: ...' \ --header 'Signature-Input: ...' \ --header 'Authorization: Bearer <access-token>' \ --header 'X-Client-Id: <client-id>' \
Scopes Granular scopes are yet to be implemented. All tokens are scoped to have both
READ and WRITE permissions
Name Permission Status readRead access across all resources ACTIVEwriteWrite access across all resources ACTIVE
HTTP Signatures Learn how to use HTTP signatures to improve API integrity