Determine Signature Base
The example signature base below is determined from the content digest example request.Signature Parameters
The field@signature-params contains an ordered list of components that make up the signature base. It is made up of two sections, fields and meta data.
"@signature-params": (fields...);meta
- fields: ordered, space (
(...) - meta: unorder, semi-colon (
;) separated and specify additional information about the cryptographic operation
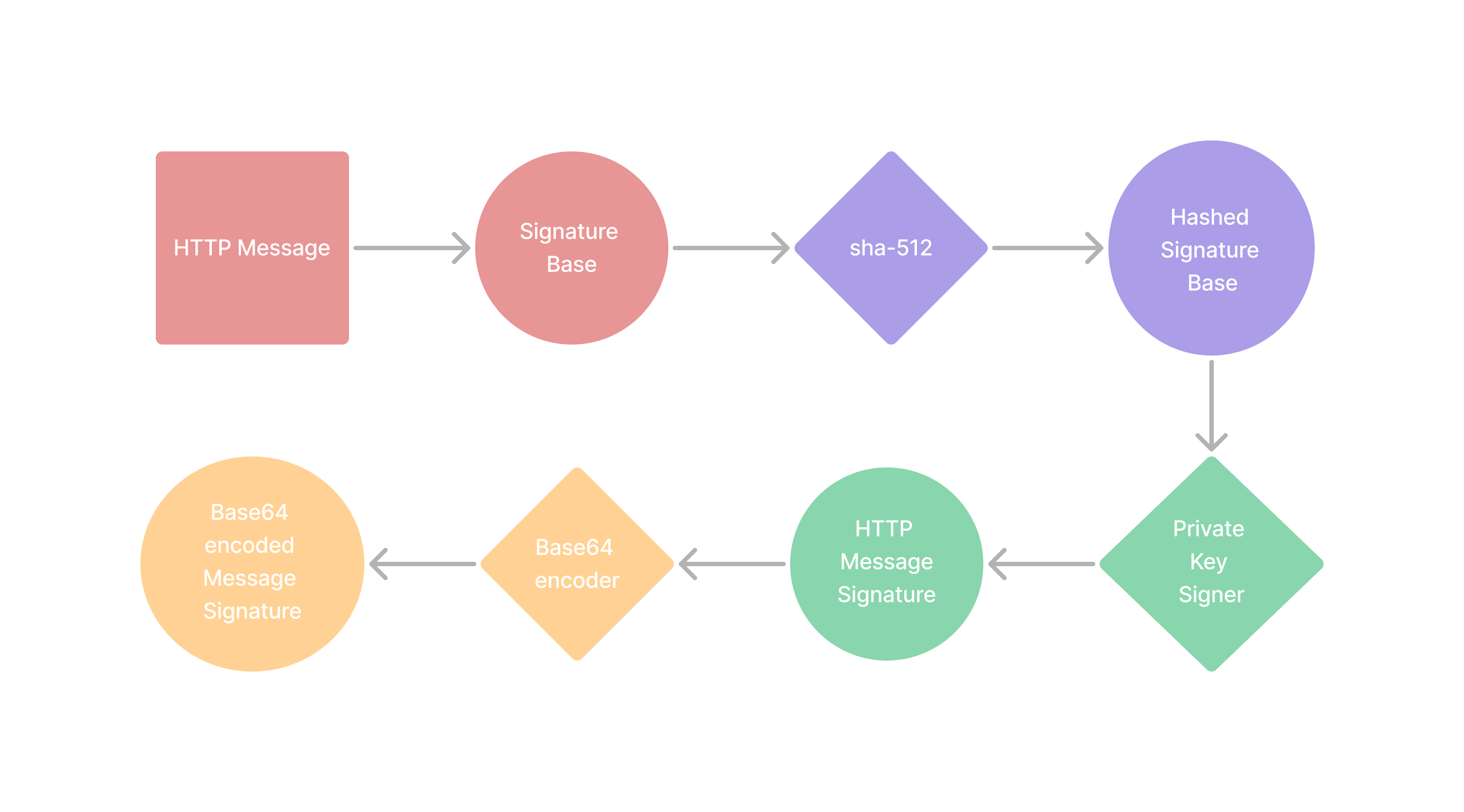
Generate Message Signature
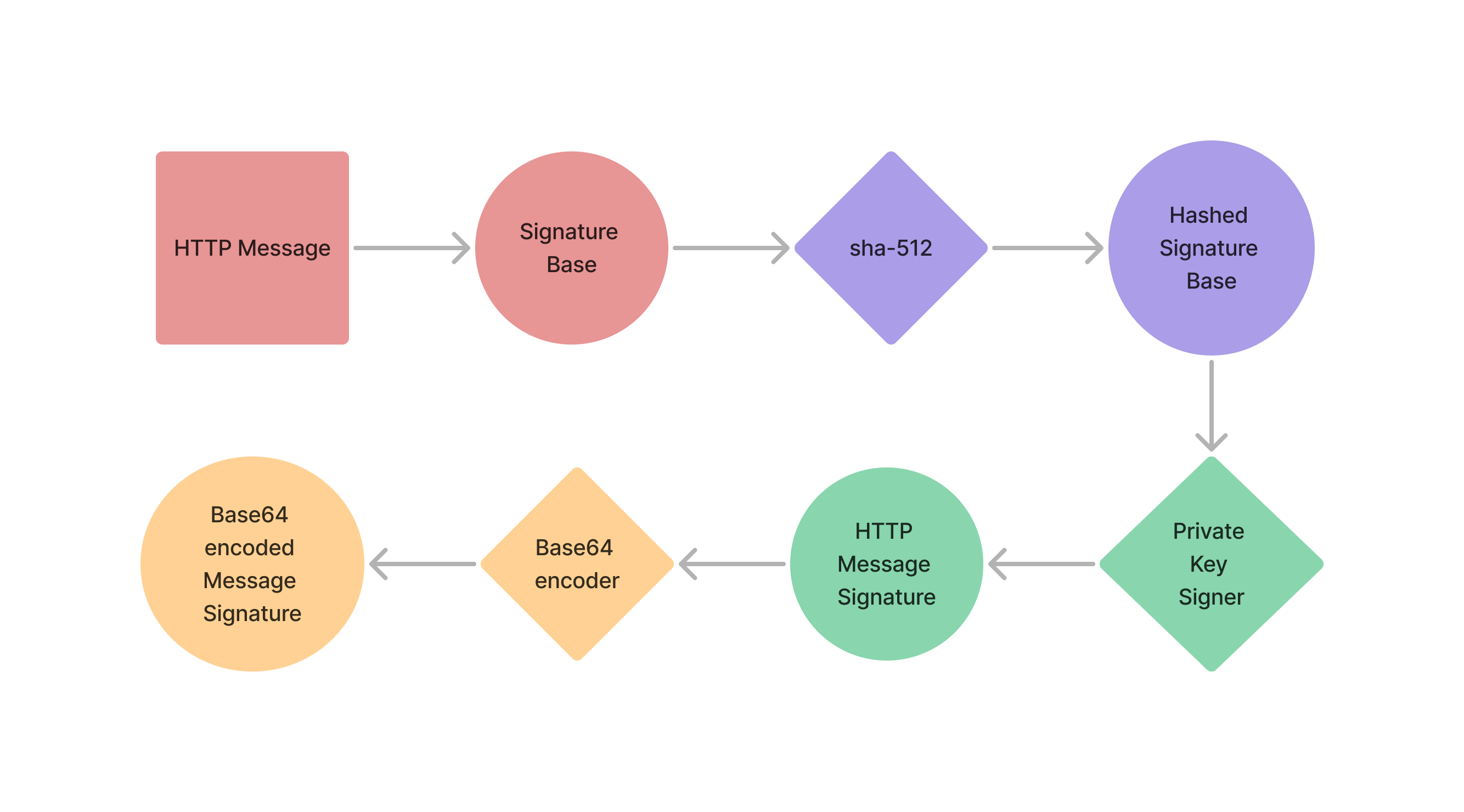
Retrieve Private Key
Identify the private key for the given environment. You should have one for:
- Staging
- Production
Determine Signature Base
Use the instructions here to determine which fields to include to generate the signature.
Calculate Signature
- Using sha-512, hash the signature base
- Sign the resulting hash with the environment specific private key.
- Base64 encode the signed hash, this is the final computed message signature (
computed-signature).
For the example request below, the
computed-signature will be OTEyMjY4...A5NTNDMEQ=Signature Input
The signature input is the same as the
@signature-params and will be passed along the header. The inputs allow for the signature to be recomputed and verified.Verify Message Signature
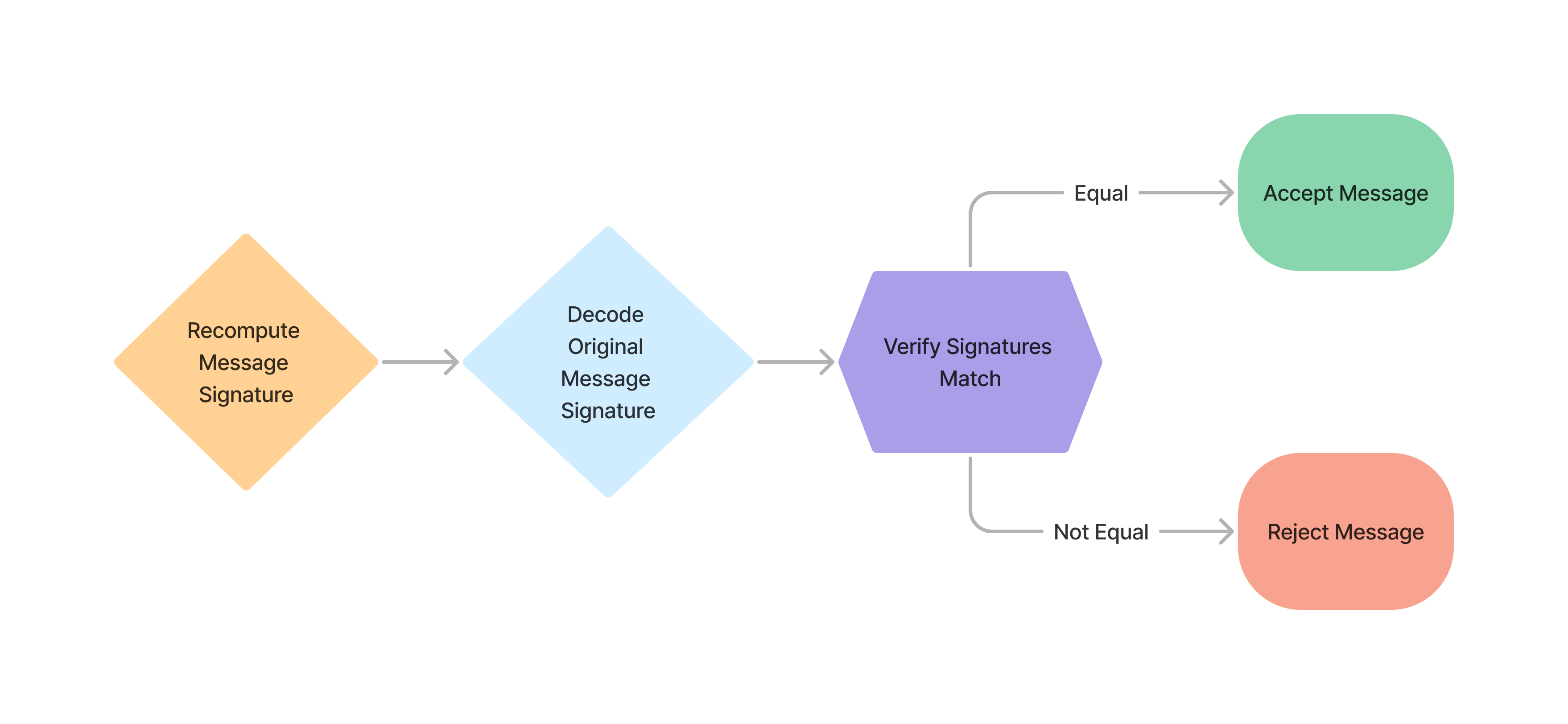
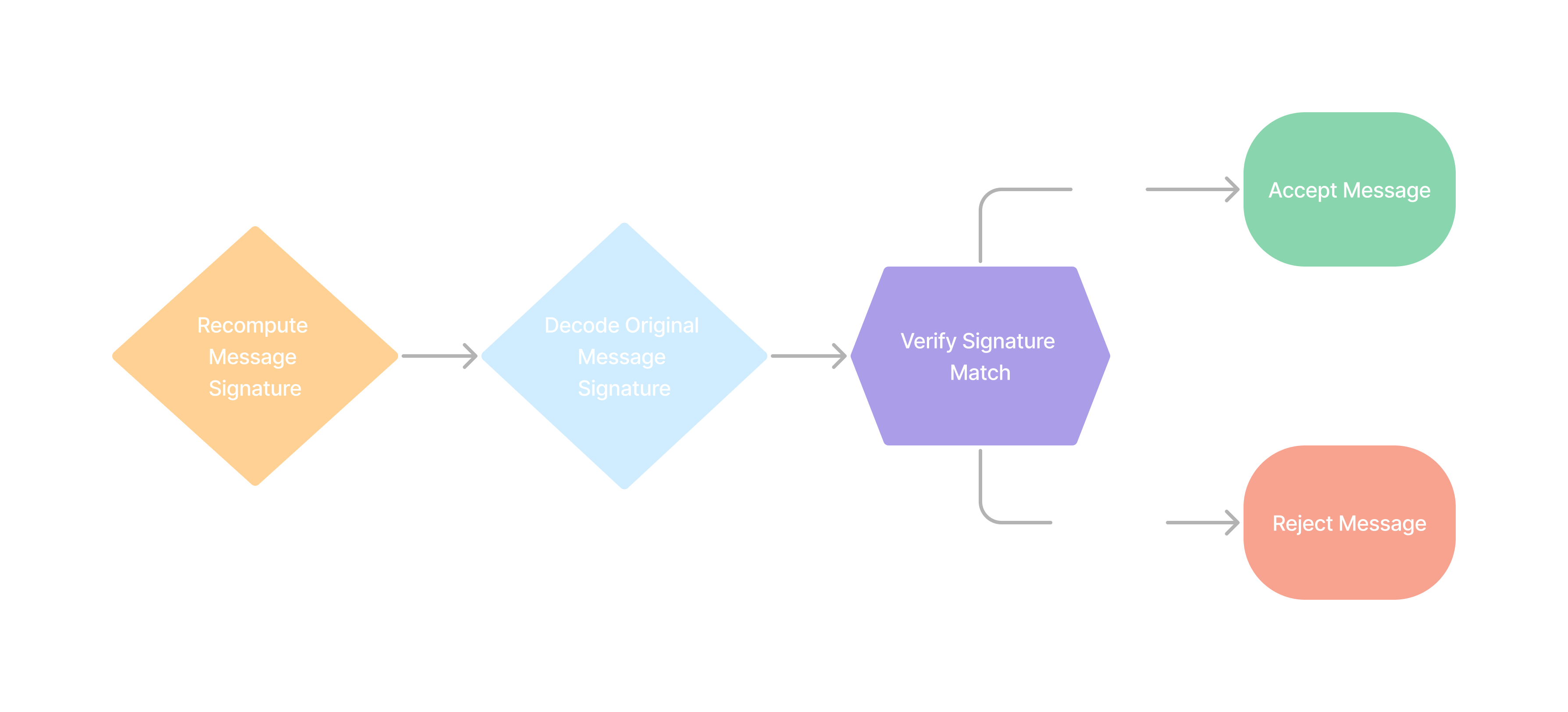
Retrieve Public Key
Identify the public key for the given environment. You should have one for:
- Staging
- Production
Recompute Message Signature
- Use the
Signature-Inputfrom the http header to determine the signature base. - Create a
sha-512digest from the signature base
We will call this
computed-message-signature.Identify Header Signature
You will need to strip the
sig1=: prefix and the : suffix to end up with the header-base64-signature.Decode Signature
Using a base64 decoder, decode the
header-base64-signature.We will call this final result, the
header-message-signature.Example Verification Code:
- Javascript
- Python
Fields
| Fields | Request Types | Required | Note |
|---|---|---|---|
Content-Type | POST, PUT, PATCH | Yes | |
Content-Digest | POST, PUT, PATCH | Yes | |
Content-Length | POST, PUT, PATCH | Yes | |
Authorization | GET, POST, PUT, PATCH, DELETE | Yes | Not required for /auth |
X-Client-Id | GET, POST, PUT, PATCH, DELETE | Yes | Not required for /auth |
X-Idempotency-Key | POST, PUT, PATCH, DELETE | Yes | |
@method | GET, POST, PUT, PATCH, DELETE | Yes | |
@target-uri | GET, POST, PUT, PATCH, DELETE | Yes | |
@path | GET, POST, PUT, PATCH, DELETE | Yes | |
@query | GET, DELETE | Yes | |
@signature-params | GET, POST, PUT, PATCH, DELETE | Yes |
Meta
| Name | Description | Required | Note |
|---|---|---|---|
keyid | This is the id of the public key sent over to pipevest. | Yes | ex: staging-pipevest-ed25519 |
created | The unix time when the cryptographic operation took place | Yes | |
expires | Unit time stamp that represents created + 100 ms | No | Not needed, but recommended |